
TL;DR
Rapid Proxy Rotation is an effective DDoS attack technique that bypasses traditional rate-based detection and mitigation mechanisms.
The use of Proxies in Layer-7-DDoS is evolving, as we wrote in 2023 and 2024 already.
In this article, we present a technique that allows attackers to bypass detection thresholds and rate limiting by leveraging proxy infrastructure. The technique is referred to as Rapid Proxy Rotation. It involves switching the source IP address for every individual request, significantly complicating detection.
A simple calculation illustrates the impact: suppose an IoT botnet consists of 1,000 IPs, each capable of generating 100 requests per second (RPS). This results in 100,000 RPS in total—but with each IP pushing 100 RPS, the activity is noisy and easily flagged.
Now consider the use of a large-scale proxy service, such as one described here, which is based on residential proxies. By proxying traffic through 10,000 rotating IPs instead of 1,000, the same 100,000 RPS workload is distributed more evenly. Each IP now only emits 10 RPS—reducing the signal per IP by 90% and making the attack much harder to detect. Scaling up the proxy pool further would reduce the per-IP RPS even more.
The proxy services we tested—particularly paid providers—support assigning a unique IP per request, which enables true Rapid Proxy Rotation. When combined with other techniques such as randomized User-Agent-Headers and multi-target or multi-vector strategies, this results in a morphing attack pattern that is extremely difficult to defend against from the defender’s perspective.
This method evades rate-based detection mechanisms and, as an additional advantage for attackers, effectively bypasses GeoIP-based blocking strategies as well.
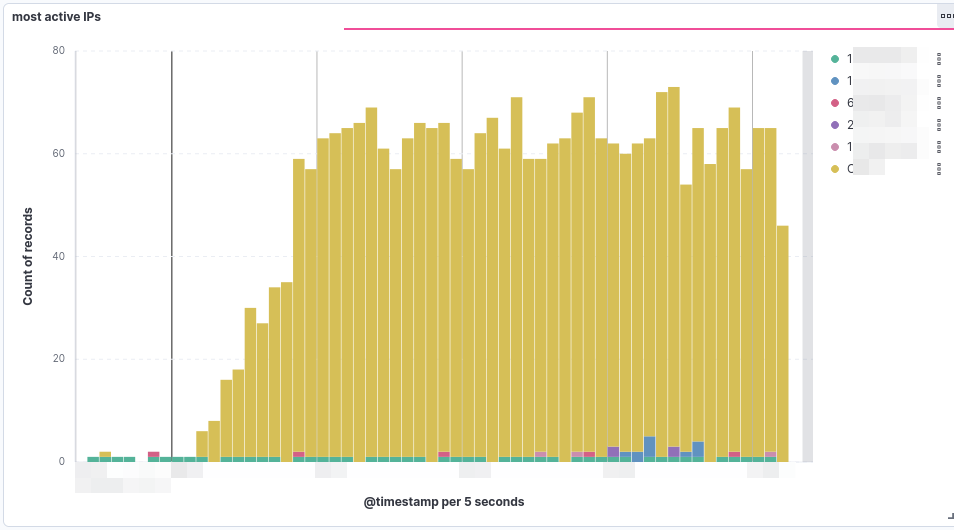
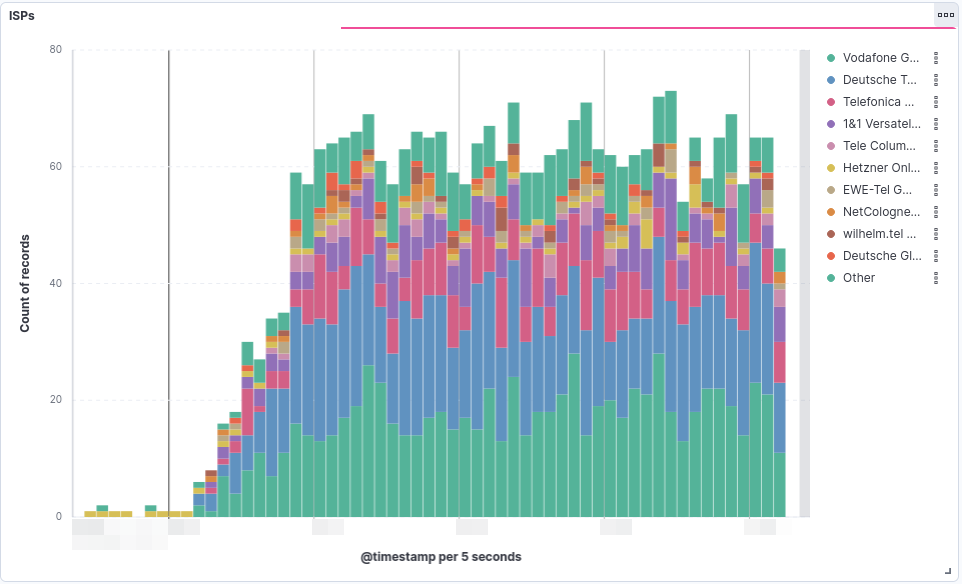
The following two visualizations support the practical viability of this method:
- The first graph displays the „Most Active IPs“ during an active attack, indirectly confirming that most IPs operate at a low and stealthy rate (1–2 RPS).
- The second graph illustrates the ISPs involved in an attack that was proxied via German infrastructure.
References
- Bypassing DDoS-Protection with Proxies, an investigation (2024)
- Bypassing GeoFencing in advanced Layer-7 DDoS Attacks (2023)
Here are several key vendor reports that discuss the use of proxies in Layer 7 DDoS attacks:
- NETSCOUT Threat Intelligence Report (Q4 2024)
- NETSCOUT observed a persistent reliance on proxy infrastructure in application-layer DDoS attacks. Proxies, particularly cloud and residential, were key enablers for HTTPS floods, accounting for over 10–20% of attack sources. Both HTTP and DNS attack traffic increasingly exhibited proxy-driven characteristics. [Netscout]
- Microsoft’s Response to Layer 7 DDoS Attacks (June 2023)
- In June 2023, Microsoft identified surges in traffic against some services, attributed to attacks likely relying on access to multiple virtual private servers (VPS) in conjunction with rented cloud infrastructure, open proxies, and DDoS tools. Microsoft Security Response Center
- StormWall Q3 2023 DDoS Attack Report
- StormWall reported a significant uptick in the deployment of mixed DDoS botnets, which utilize various types of malware in a single attack campaign. These botnets often employ proxies to mask the origin of traffic, enhancing the complexity and resilience of attacks. stormwall.network
- Cloudflare DDoS Threat Report for Q4 2024
- Cloudflare mitigated 6.9 million DDoS attacks in Q4 2024, with 51% being HTTP DDoS attacks. The majority of these attacks (73%) were launched by known botnets, many of which utilize proxy services to obfuscate traffic sources. The Cloudflare Blog
- Akamai’s Retrospective on DDoS Trends in 2023
- Akamai noted that throughout 2023, DDoS attacks became more frequent and sophisticated, often employing multiple vectors. The use of proxies was highlighted as a method to enhance the stealth and effectiveness of Layer 7 attacks. Akamai





